Introduction:
Mule Properties can be encrypted to keep your sensitive data like Passwords, ClientID, Access Key, Secret key. Secure property is Mulesoft Provided module. We can be used to encrypt a .properties file or .yaml file. Generally, in properties files, we store information like Client ID, Secret, Access Key, Secret Key, User Id, Password, Secure Tokens, Oauth Token etc.
We need to encrypt the data inside any property files to restrict unauthorized access and to protect the data. Secure Property Placeholder is an important standard for keeping our sensitive data like User ID and Password secure (encrypted/cypher-text) in the Property file. Data is stored in the property file as key value pair. This property file can store information like User ID, Password, Tokens, Keys etc. After storing these data in the property file, we need encryption to restrict unauthorized access and to protect the data. To do this we are using the MuleSoft’s Secure Property Placeholder.
Creating Secure Properties
Step 1: Create a configuration properties file.
Step 2: We can encrypt the whole file or encrypt individual property.
For individual property, we can define secure properties in the file by enclosing the encrypted values between the sequence! [value].
Step 3: Configure the file in the project with the Mule Secure Configuration Properties Extension module dependency. The file must point to or include the decryption key.
Create a Configuration Properties File: The Secure configuration properties is to create the properties/configuration file (either .properties or .yaml). The Properties/Configuration file will be placed into `src/main/resource` folder.
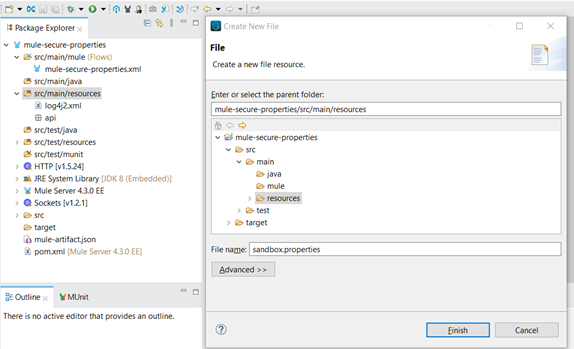
The Properties/configuration file are having the non-encrypted values as below:
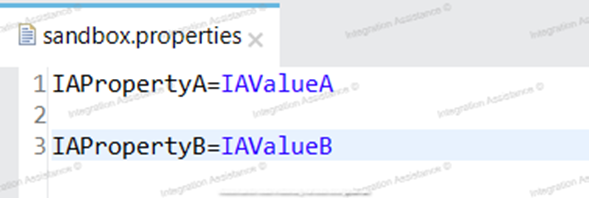
Define Secure Configuration Properties
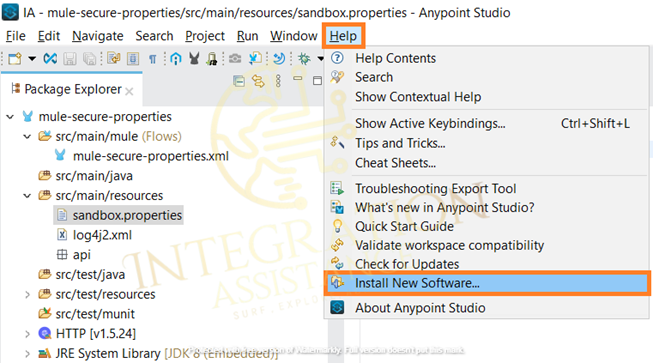
1. Adding the Premium Security Connector in AnyPoint Studio
Open Anypoint Studio -> Go to Help -> Select Install New Software
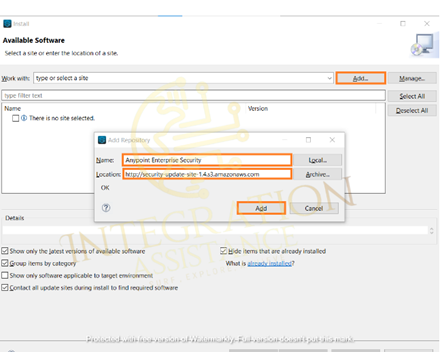
Click the Add button and it will open a window, provide Name as Anypoint Enterprise Security, and provide location as http://security-update-site-1.4.s3.amazonaws.com and press ok.
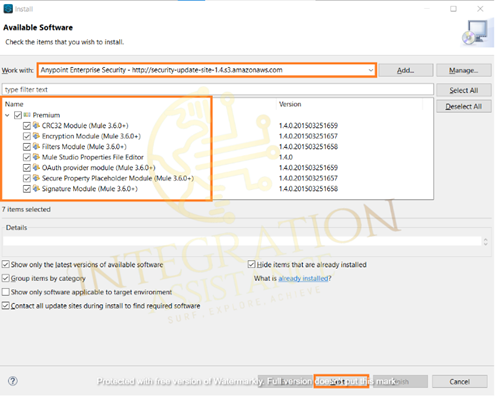
Go to the work drop-down and check Anypoint Enterprise Security — in the dropdown list.
Select it and select the Premium checkbox -> click Next — accept the policy and finish.
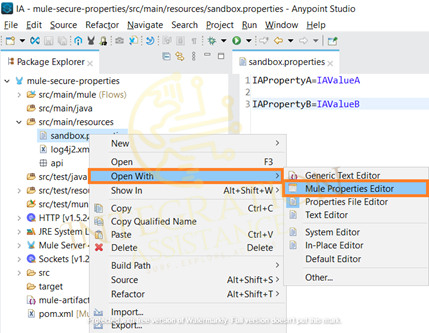
Now go to the application and right-click on sandbox.properties and go to -> Open with -> Mule Properties Editor. Now your property file is open in the table editor view.
Double click on any key. It will open a new window. Now press the button Encrypt.
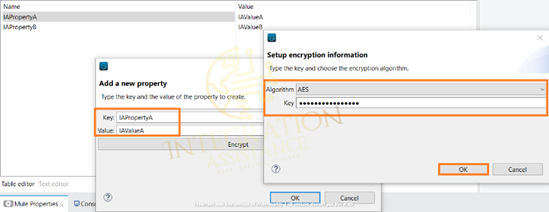
In the next window specify the ‘algorithm’ (Algorithm used to encrypt/decrypt the value example- AES, Blowfish) and provide an encryption key(key size must be at least: ’16’ if it is AES algorithm) to encrypt. Press the OK button.
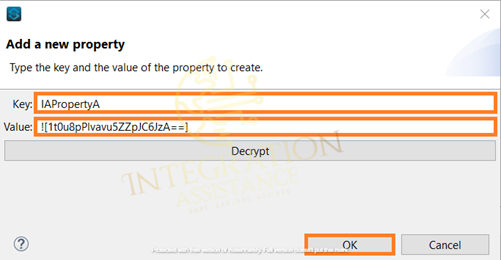
Similarly, you can encrypt the rest of the properties and open the file with a text editor.

***Note: We cannot encrypt the YAML file this way as after the encryption process all the property key alignment will be rearranged. ***
But encryption of YAML file can be achieved using Java encryption JAR
Encrypt Properties Using the Secure Properties Tool(jar)
Download Secure-properties-tool.jar and put it into the same folder, where we saved the unencrypted configuration YAML.
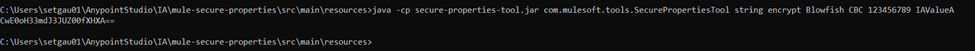
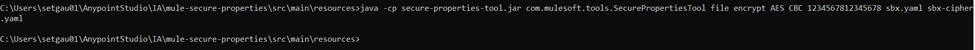
Use the following syntax to encrypt or decrypt all the content of a properties file:
String Level Example
File Level Example
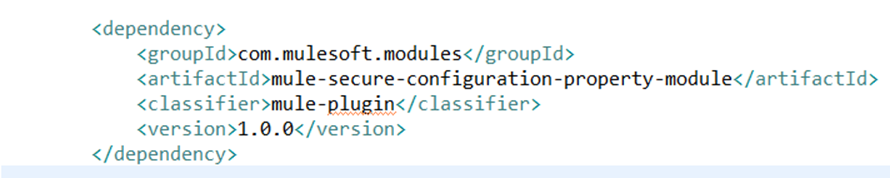
2. Configuring Secure Property Module and add dependency in Project
Add the secure property module in your project and configure the same.
Maven dependency:
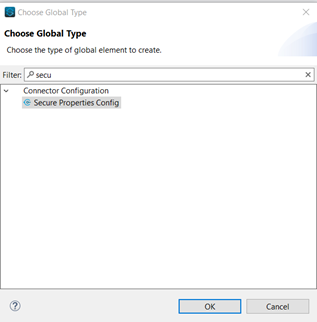
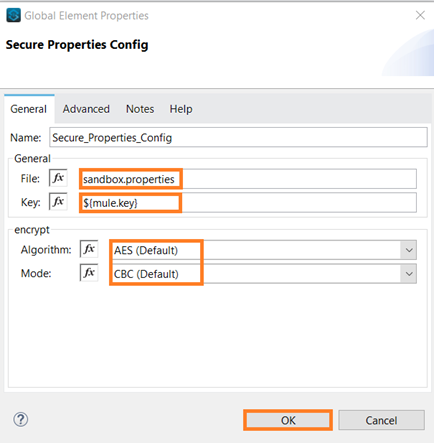
3. Create Global Configuration and Provide encryption /decryption key:
This token will be passed in runtime configuration as program argument example: -Dtoken=1234567812345678. And define the correct Algorithm and mode used for encryption.
Go to Global Elements → Create → -> select the Secure Properties Config from Connector Configuration.
4. Use of Secure Property:
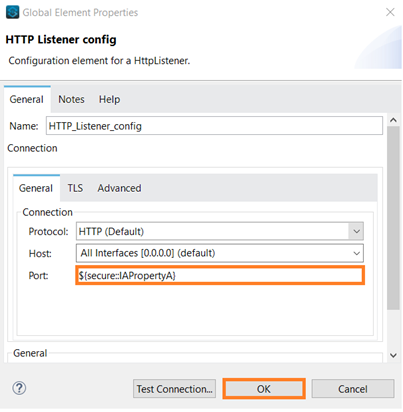
In any global configuration you can use this secure property as ${secure:: property.name}.
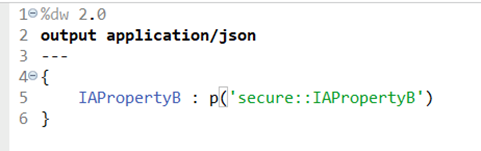
In dwl we can also use secure property as p(‘secure:: property.name’)
In this below example we used http port as ${secure:: http.port} and decrypted_username_value: p(‘secure::username’)
Please note, the decryption process will be done implicitly by the Mule Runtime engine and this requires only the Key (passed as VM argument) which was used to encrypt the password.